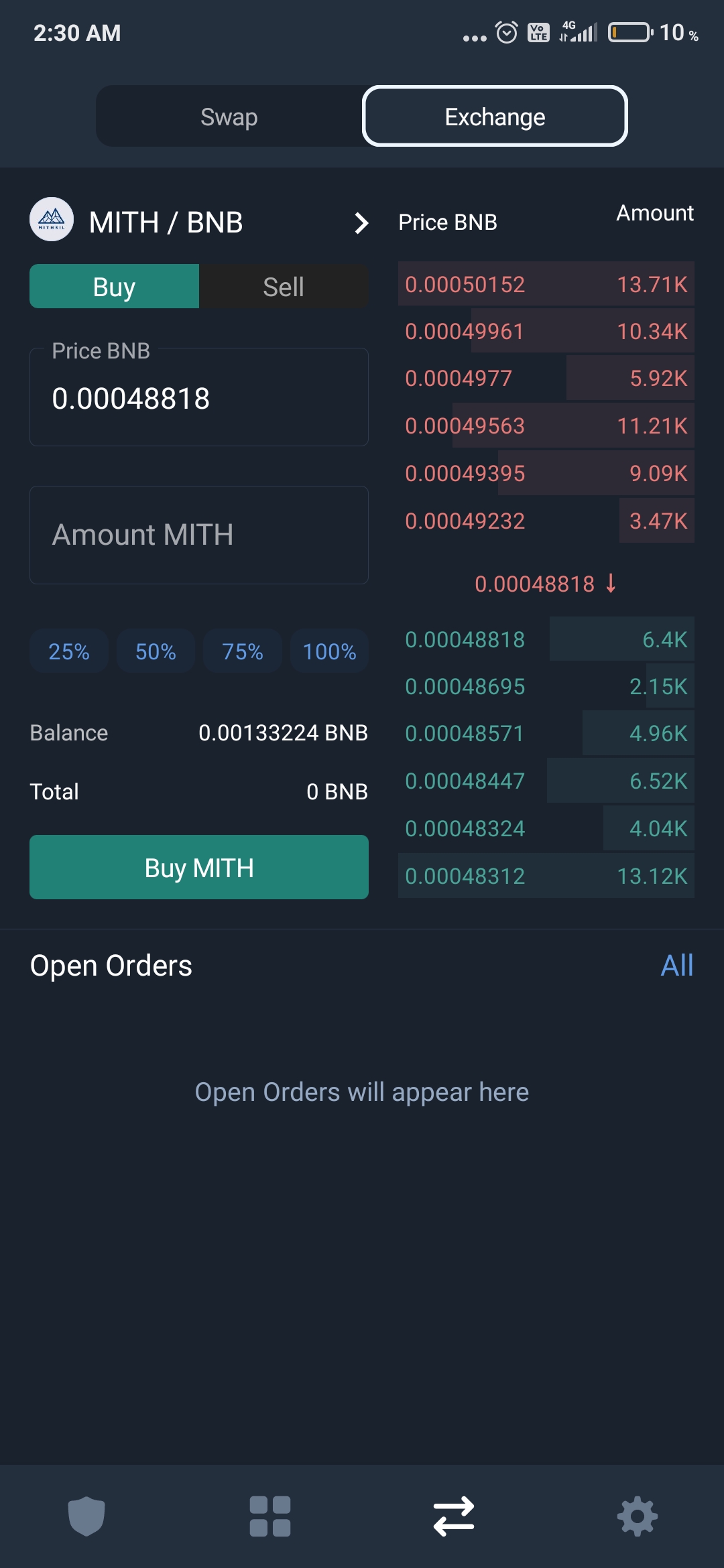
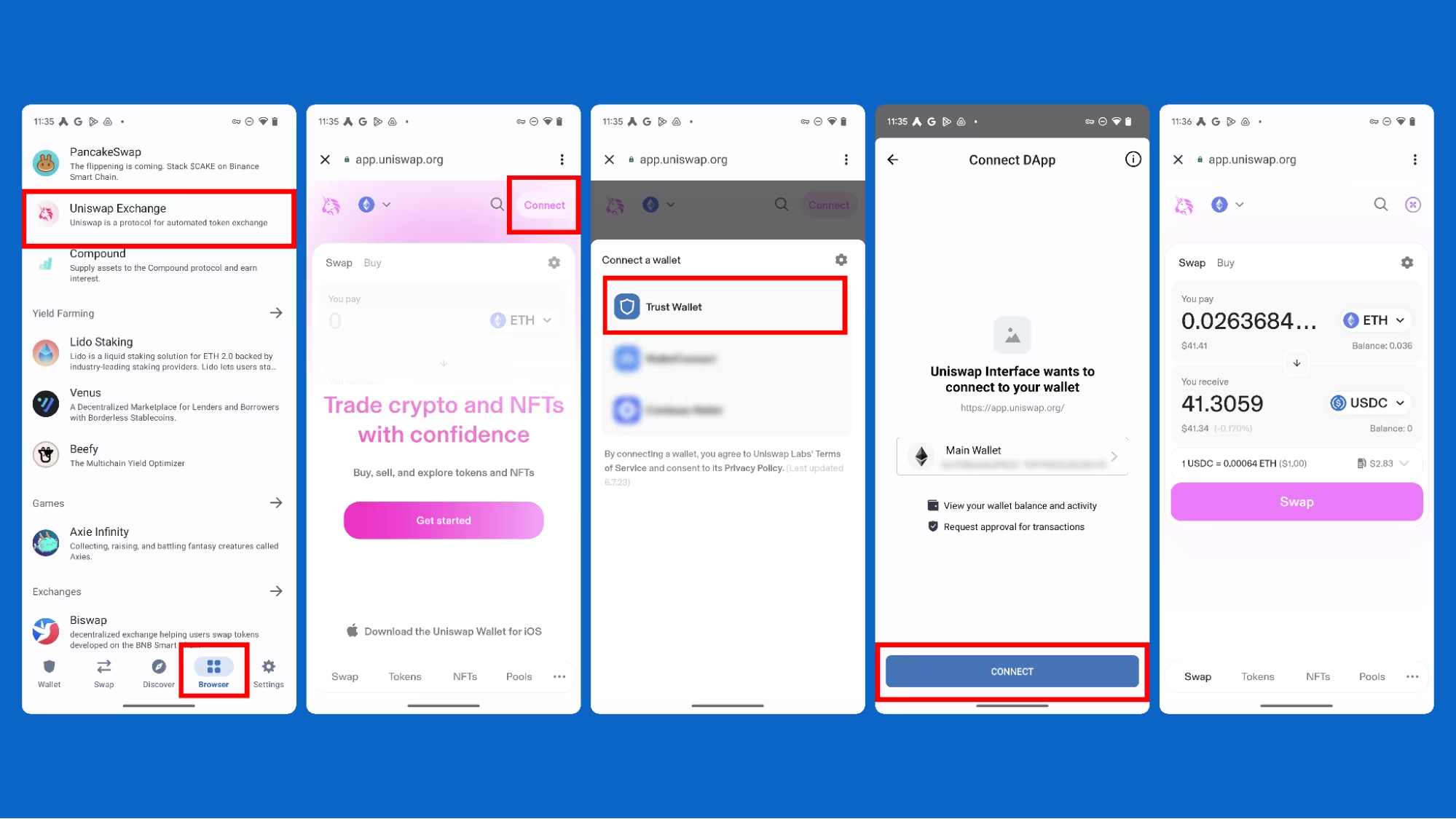
Yes, funds can be stolen from a Trust Wallet if your private keys or seed phrases are compromised through phishing or malware.
Common Threats
Recognizing and protecting against common threats is essential to secure your MetaMask wallet. Here’s a brief overview of two major threats: phishing attacks and malware, including keyloggers.
Phishing Attacks
- Fake Websites and Emails:
- Website Spoofing: Attackers create look-alike sites to steal your credentials.
- Email Scams: Scammers send emails pretending to be from MetaMask to collect sensitive information.
- Social Engineering Tactics:
- Impersonation: Attackers pose as MetaMask support to trick you into revealing private keys.
- Urgency and Fear: Messages may create a sense of urgency to make you act without thinking.
Malware and Keyloggers
- Malicious Software:
- Keyloggers: These capture your keystrokes, stealing passwords and private keys.
- Trojan Horses: Disguised as legitimate software, they can control your device.
- Distribution Methods:
- Infected Downloads: Downloading from untrusted sources can install malware.
- Phishing Links: Clicking on malicious links can download harmful software.
Protecting Your Seed Phrase
Your MetaMask seed phrase is the key to accessing your wallet and digital assets. Safeguarding it is crucial for security. Here are effective methods to protect your seed phrase.
Secure Storage Methods
- Physical Storage:
- Write Down on Paper: Write your seed phrase on paper and store it in a safe, such as a fireproof and waterproof safe. This method keeps it offline and away from digital threats.
- Engraving on Metal: For added durability, consider engraving your seed phrase on a metal plate. This makes it resistant to fire and water damage, ensuring long-term preservation.
- Multiple Secure Locations:
- Distribute Across Locations: Store copies of your seed phrase in multiple secure locations. This reduces the risk of total loss if one location is compromised.
- Use Trusted Guardians: Consider giving copies to trusted family members or using professional vault services for added security.
Avoiding Digital Storage
- Avoid Storing on Devices:
- No Screenshots or Digital Notes: Do not store your seed phrase on your phone, computer, or cloud services. Digital storage methods are vulnerable to hacking and malware.
- Disable Auto-Backup: Ensure that automatic backup services do not save your seed phrase inadvertently.
- Risks of Online Exposure:
- Phishing and Hacks: Storing your seed phrase online exposes it to potential phishing attacks and hacking attempts.
- Physical Theft: Devices storing your seed phrase can be stolen or accessed by unauthorized individuals.
Enabling Two-Factor Authentication
Two-Factor Authentication (2FA) adds an extra layer of security to your online accounts, including services connected to MetaMask. Here’s how to set up 2FA and its benefits.
How to Set Up 2FA
- Choosing a 2FA Method:
- Authenticator Apps: Use apps like Google Authenticator or Authy. These generate time-based codes that you enter along with your password.
- SMS Codes: Some platforms send verification codes via SMS. While less secure than authenticator apps, it still adds a layer of protection.
- Setting Up 2FA on Accounts Linked to MetaMask:
- Login to Your Account: Access the security settings of your account (e.g., email, exchanges) that supports 2FA.
- Enable 2FA: Follow the prompts to enable 2FA, selecting your preferred method (app or SMS).
- Scan the QR Code: If using an authenticator app, scan the QR code provided by the service to link it with the app.
- Enter the Verification Code: Input the generated code from your authenticator app or the SMS code to complete the setup.
- Securing Your 2FA Backup Codes:
- Store Securely: Write down the backup codes provided during setup and store them in a secure place, separate from your devices.
- Avoid Digital Storage: Like with your seed phrase, avoid storing these codes digitally to prevent unauthorized access.
Benefits of 2FA
- Enhanced Account Security:
- Extra Verification Step: 2FA requires a second form of authentication, significantly reducing the risk of unauthorized access even if your password is compromised.
- Protection Against Phishing: It adds a layer of security that can prevent attackers from accessing your accounts, even if they obtain your login credentials through phishing.
- Reduced Risk of Unauthorized Transactions:
- Secure Access to Linked Services: Accounts linked to MetaMask that support 2FA, such as email and cryptocurrency exchanges, are better protected against unauthorized access.
- Multi-Factor Barrier: Combining 2FA with strong passwords and secure practices creates a robust defense against unauthorized transactions and account breaches.
Keeping Your App Updated
Regular updates are essential to maintain the security and functionality of your MetaMask app. Here’s why keeping your app updated is crucial and how to enable automatic updates.
Importance of Updates
- Security Enhancements:
- Patch Vulnerabilities: Updates often include patches for newly discovered security flaws. Keeping your app updated helps protect against potential exploits.
- Improved Protection: Each update enhances the app’s security measures, providing better protection against emerging threats and attacks.
- New Features and Improvements:
- Access to Latest Features: Updates bring new functionalities and user interface improvements, enhancing your experience and capabilities with MetaMask.
- Performance Enhancements: Regular updates optimize the app’s performance, ensuring it runs smoothly and efficiently.
- Compliance with Blockchain Changes:
- Network Compatibility: Updates ensure that MetaMask remains compatible with the latest changes in blockchain protocols and standards.
- Regulatory Compliance: Staying updated helps MetaMask adhere to evolving industry regulations and best practices.
How to Enable Automatic Updates
- For Mobile Devices:
- iOS Devices:
- Open Settings: Go to your device’s “Settings.”
- Navigate to App Store: Scroll down and select “App Store.”
- Enable Automatic Updates: Toggle the switch for “App Updates” to enable automatic updates for all apps, including MetaMask.
- Android Devices:
- Open Google Play Store: Launch the Google Play Store app.
- Access Settings: Tap on your profile icon and go to “Settings.”
- Enable Auto-Update: Select “Network preferences” and then “Auto-update apps.” Choose “Over any network” or “Over Wi-Fi only” for automatic updates.
- iOS Devices:
- For Browser Extensions:
- Chrome:
- Access Extensions Page: Go to “chrome://extensions/” in your browser.
- Enable Developer Mode: Toggle “Developer mode” in the top right corner.
- Check for Updates: Click on the “Update” button to manually check for and install updates for all extensions, including MetaMask.
- Firefox:
- Open Add-ons Manager: Go to “about
” in your browser.
- Enable Automatic Updates: Click on the gear icon and select “Update Add-ons Automatically.” MetaMask will update itself whenever a new version is available.
- Open Add-ons Manager: Go to “about
- Chrome:
- Stay Informed:
- Follow Official Channels: Subscribe to MetaMask’s updates on their official website and social media for news on the latest features and improvements.
- Check App Stores Regularly: Regularly visit the app store or extension store to ensure your MetaMask is up-to-date.
What to Do If Your Funds Are Stolen
If you discover that your funds have been stolen, acting quickly and following the right steps can help you mitigate the damage and potentially recover your assets. Here’s what you should do immediately and how to report the incident to authorities and support teams.
Immediate Steps to Take
- Document the Incident:
- Record Transaction Details: Take screenshots or note down the transaction ID, the stolen amount, and the address to which the funds were sent. This information is crucial for reporting and tracking.
- Check Activity Logs: Review the activity logs in your MetaMask wallet to identify unauthorized transactions and any related suspicious activity.
- Secure Your Account:
- Disconnect from dApps: Immediately disconnect your wallet from any decentralized applications (dApps) to prevent further unauthorized transactions.
- Change Passwords: Change the passwords for your MetaMask account and any related accounts, such as your email and exchange accounts. This helps prevent additional breaches.
- Revoke Permissions: Use tools like Etherscan’s Token Approval Checker to revoke any permissions granted to unknown or suspicious addresses.
- Transfer Remaining Funds:
- Move Assets to a Secure Wallet: If you have any remaining funds or assets, transfer them to a new wallet with a newly generated seed phrase. Ensure that this new wallet is secure and not compromised.
Reporting to Authorities and Support
- Contact MetaMask Support:
- Submit a Report: Visit the MetaMask Support Page and submit a detailed report of the theft, including all documented transaction details and any relevant screenshots.
- Follow Up: Keep in touch with the MetaMask support team for updates and further instructions. They may provide guidance on steps to take and how to protect your account.
- Report to Blockchain Explorers:
- Flag the Stolen Funds: Use blockchain explorers like Etherscan to flag the stolen transaction and address as compromised. This can help alert other users and exchanges to the theft.
- Track Transactions: Monitor the blockchain for any movement of the stolen funds. This tracking can provide valuable information for authorities and investigators.
- Notify Law Enforcement:
- File a Police Report: Contact your local law enforcement agency and file a report. Provide them with all the documented evidence and transaction details.
- Engage Cybercrime Units: Some regions have specialized cybercrime units. Reporting to these units can increase the chances of recovering your assets.
- Reach Out to Crypto Exchanges:
- Alert Relevant Exchanges: If the stolen funds are sent to a known cryptocurrency exchange, contact their support team immediately. Provide them with transaction details and request they freeze the funds or account.
Best Practices for Wallet Security
Maintaining strong security practices is essential to protect your digital assets in MetaMask. Here are some best practices, including using hardware wallets and conducting regular security audits.
Using Hardware Wallets
- Enhanced Security for Private Keys:
- Offline Storage: Hardware wallets store your private keys offline, making them inaccessible to online threats and hacking attempts. This reduces the risk of your keys being exposed to malware or phishing attacks.
- Physical Confirmation: Transactions must be confirmed physically on the hardware device, adding an extra layer of security. This prevents unauthorized transactions even if your computer is compromised.
- Integration with MetaMask:
- Compatible Devices: Popular hardware wallets like Ledger and Trezor integrate seamlessly with MetaMask. This allows you to use the security of a hardware wallet while enjoying the convenience of MetaMask’s interface.
- Setup Process: To connect a hardware wallet to MetaMask, select the “Connect Hardware Wallet” option in MetaMask. Follow the on-screen instructions to link your hardware device securely.
- Best Practices for Hardware Wallet Use:
- Keep Firmware Updated: Regularly update your hardware wallet’s firmware to the latest version to benefit from improved security features and bug fixes.
- Secure Physical Storage: Store your hardware wallet in a safe place when not in use, preferably in a fireproof and waterproof location. Avoid leaving it connected to your computer when not needed.
Regular Security Audits
- Conducting Personal Audits:
- Review Permissions and Connections: Regularly check the permissions granted to dApps and remove any that are no longer needed or seem suspicious. Use tools like Etherscan’s Token Approval Checker for this purpose.
- Monitor Account Activity: Frequently review your MetaMask transaction history and account activity for any unusual or unauthorized transactions. Immediate detection can help mitigate damage.
- Professional Security Audits:
- Engage Security Experts: Consider hiring cybersecurity professionals to perform detailed audits of your wallet’s security setup, especially if you manage significant assets.
- Blockchain Security Firms: Some firms specialize in auditing blockchain security and can provide in-depth assessments of your MetaMask and overall security posture.
- Updating Security Practices:
- Stay Informed: Keep up-to-date with the latest security practices and threats in the cryptocurrency world. Follow MetaMask’s updates and guidelines on security.
- Change Passwords Regularly: Update your MetaMask and related account passwords periodically to reduce the risk of unauthorized access.